Leverage Cloud Services for Improved Information Safety
In today's digital landscape, the ever-evolving nature of cyber hazards demands a positive technique in the direction of protecting sensitive data. Leveraging cloud services presents a compelling service for organizations looking for to strengthen their information safety actions. By delegating trustworthy cloud service companies with information administration, services can tap into a riches of protective features and sophisticated technologies that boost their defenses versus harmful actors. The concern occurs: exactly how can the usage of cloud services revolutionize information security techniques and give a robust shield versus prospective vulnerabilities?
Importance of Cloud Security
Ensuring robust cloud security procedures is vital in protecting delicate data in today's electronic landscape. As organizations significantly depend on cloud services to save and process their information, the requirement for solid safety procedures can not be overemphasized. A breach in cloud safety can have severe repercussions, varying from monetary losses to reputational damage.
One of the main reasons cloud safety is critical is the shared responsibility design employed by most cloud provider. While the copyright is accountable for safeguarding the infrastructure, clients are accountable for safeguarding their information within the cloud. This division of obligations emphasizes the importance of carrying out durable safety and security measures at the customer degree.
Moreover, with the expansion of cyber dangers targeting cloud settings, such as ransomware and data breaches, companies must stay attentive and aggressive in mitigating dangers. This includes regularly updating safety and security procedures, checking for dubious tasks, and enlightening staff members on ideal practices for cloud security. By prioritizing cloud security, organizations can better protect their sensitive information and support the trust fund of their consumers and stakeholders.
Information Security in the Cloud
File encryption in the cloud generally includes making use of cryptographic formulas to scramble data into unreadable styles. This encrypted data can just be decoded with the corresponding decryption secret, which includes an added layer of security. Additionally, lots of cloud company provide security devices to safeguard information at remainder and in transportation, enhancing general information defense. Executing robust file encryption practices along with other safety and security procedures can significantly reinforce an organization's defense against cyber threats and safeguard important information saved in the cloud.
Secure Information Back-up Solutions
Information back-up options play a critical duty in making certain the strength and safety of data in the event of unexpected cases or information loss. Protected data backup remedies are crucial parts of a robust data protection method. By on a regular basis backing up data to safeguard cloud servers, companies can reduce the risks linked with information loss due to cyber-attacks, equipment failures, or human error.
Implementing safe and secure information backup services includes choosing trusted cloud solution companies that offer encryption, redundancy, and information stability steps. Additionally, data stability checks make certain that the backed-up information stays unchanged and tamper-proof.
Organizations needs to establish automatic back-up routines to make certain that data is constantly and efficiently supported without manual intervention. Normal testing of information repair procedures is likewise crucial to guarantee the performance of the backup solutions in recovering information when required. By investing in protected information backup options, companies can improve their data security pose and decrease the effect of possible information breaches or disturbances.
Duty of Gain Access To Controls
Executing he said strict access controls is imperative for preserving the safety and security and integrity of delicate information within organizational systems. Gain access to controls work as an important layer of protection versus unapproved gain access to, guaranteeing that only authorized people can view or adjust delicate information. By specifying who can gain access to specific resources, companies can restrict the danger of data breaches and unapproved disclosures.

Frequently evaluating and updating gain access to controls is necessary to adjust to organizational changes and advancing protection dangers. Continuous monitoring and bookkeeping of gain access to logs can help identify any type of suspicious tasks and unauthorized access efforts immediately. Overall, durable access controls are basic in securing sensitive info and mitigating security dangers within organizational systems.
Conformity and Regulations
Regularly making sure compliance with appropriate regulations and requirements is vital for organizations to maintain data safety and privacy steps. In the world of cloud services, where data is often stored and refined externally, adherence to industry-specific guidelines such as GDPR, HIPAA, or PCI DSS is essential. These guidelines mandate specific information handling methods to safeguard delicate information and guarantee customer privacy. Failure to abide by these laws can result in serious fines, including fines and lawsuits, harming an organization's credibility and trust fund.
Lots of service providers provide security capacities, gain access to controls, and audit trails to aid companies satisfy information safety standards. By leveraging certified cloud services, companies can improve their data security pose while meeting governing responsibilities.
Verdict
To conclude, leveraging cloud services for improved data protection is crucial for organizations to shield sensitive details from unauthorized gain access to and possible breaches. By additional hints applying robust cloud protection procedures, including information encryption, safe back-up remedies, gain access to controls, and compliance with policies, companies can gain from advanced protection measures and experience used by cloud company. This assists minimize risks efficiently and makes sure the discretion, integrity, and schedule of information.
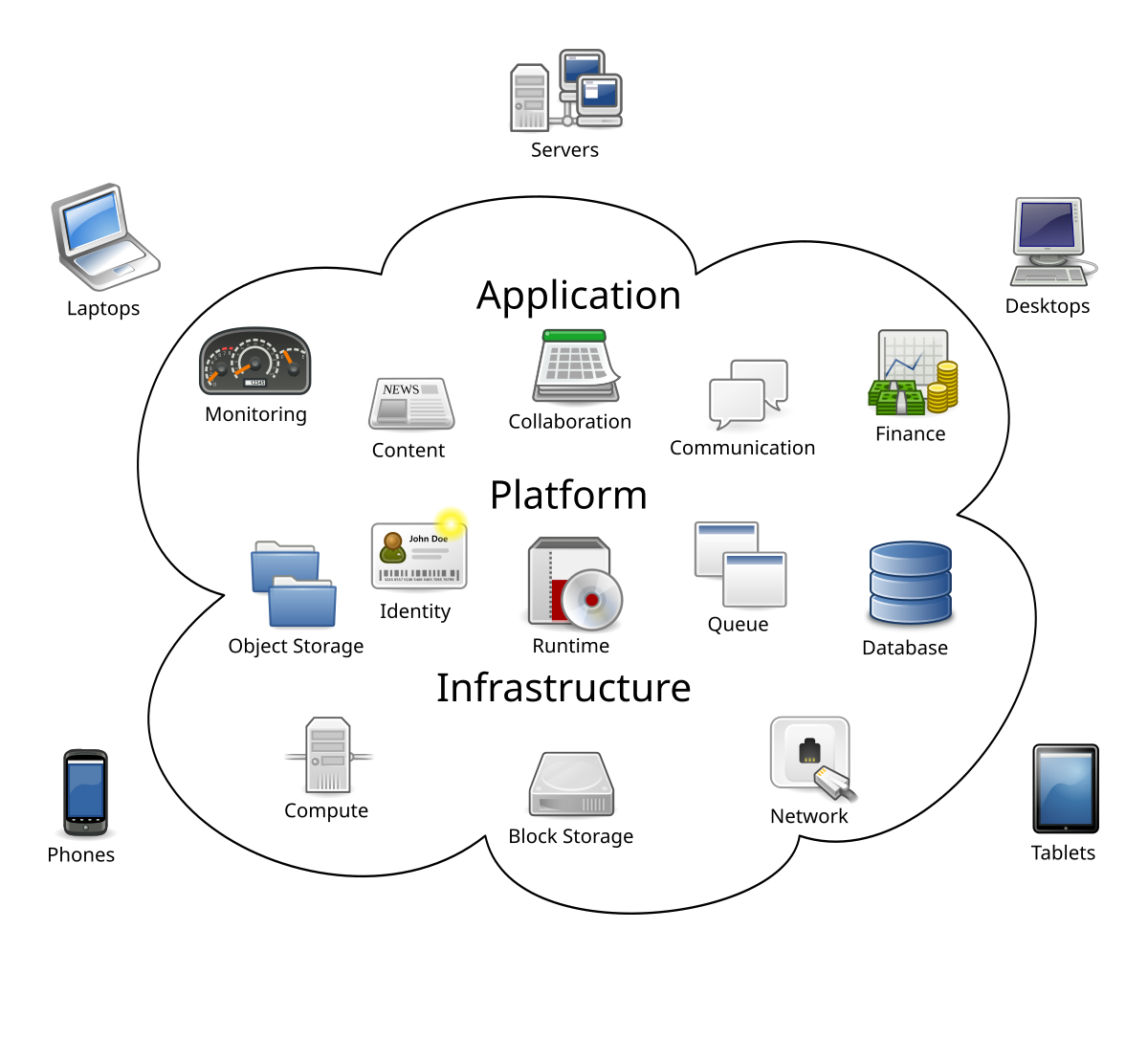
Information why not find out more backup solutions play a crucial function in making sure the resilience and security of information in the event of unexpected cases or data loss. By consistently backing up data to safeguard cloud servers, organizations can minimize the dangers associated with information loss due to cyber-attacks, hardware failings, or human error.
Executing safe and secure data backup solutions entails choosing reliable cloud solution providers that provide security, redundancy, and data honesty measures. By spending in secure information backup solutions, services can enhance their information safety posture and lessen the impact of prospective information breaches or disturbances.